Details
-
Bug
-
Status: Open (View Workflow)
-
Major
-
Resolution: Unresolved
-
None
-
None
-
None
-
None
Description
... and, furthermore, the server requires that information to be sent in plaintext, and irreversibly updates its assessment of the client capabilities for this connection based on it (see MDEV-31585).
Spinning this off from my comment on CONC-648. (Like CONC-648, this is another TLS-related vulnerability.)
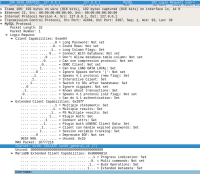
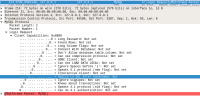
As I showed there, MariaDB clients including Connector/C send a great deal of identifying information about themselves in plaintext in the initial "login request" packet, even when they subsequently switch to TLS, and then resend a login request packet over the TLS channel:
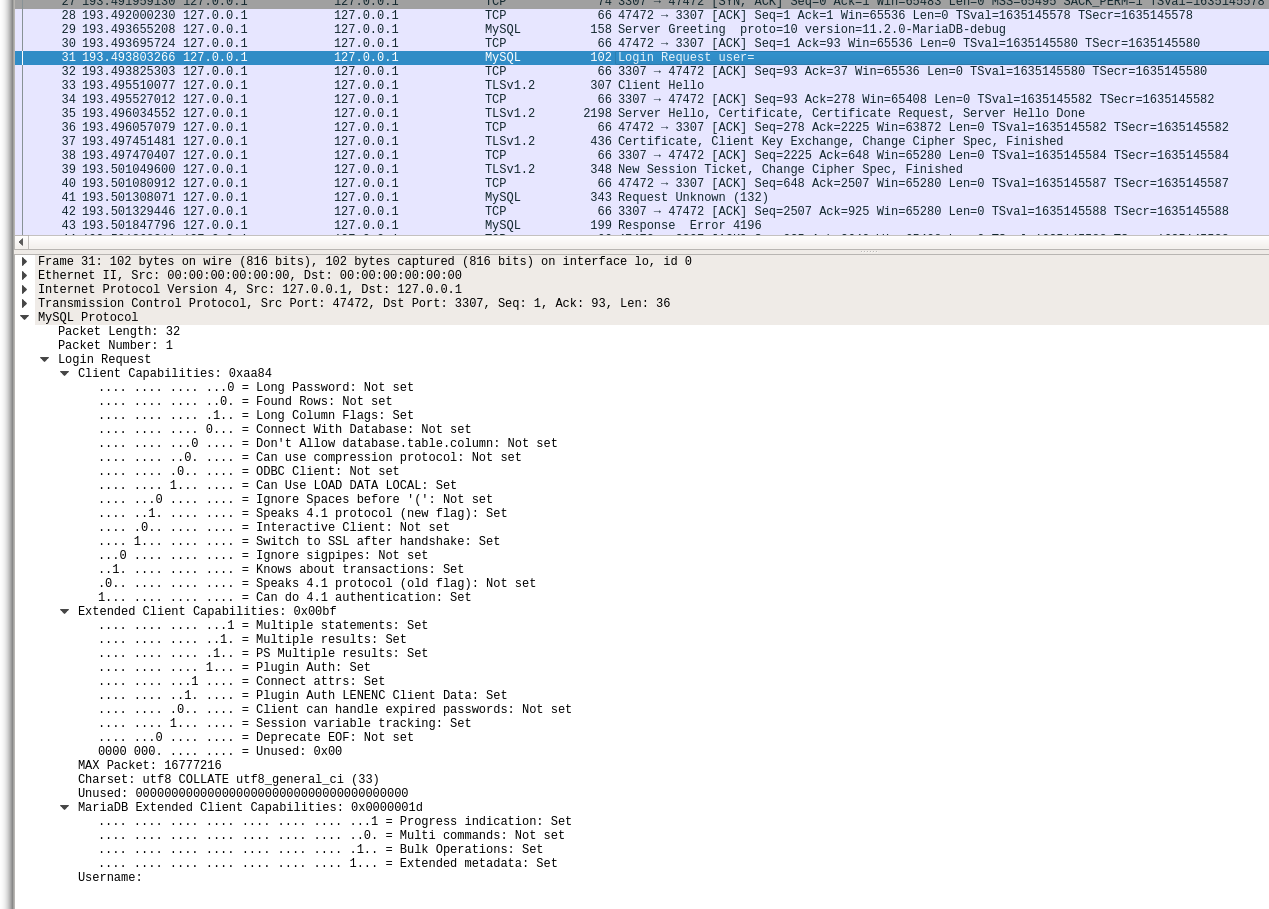
This information includes the client capability bits, the client's MAX_ALLOWED_PACKET size, and the client's charset.
Copying from there:
This makes MariaDB client-server connections an exploitable and target-rich environment for pervasive MITM attackers. A government agency could, for example, fingerprint the plaintext client+server greeting packets to determine the exact versions, pull out the ones that appear to be from interesting parts of the world based on the plaintext preferred client charset, and manipulate them in various ways with MITM and downgrade attacks using this vulnerability, as well as the long-known
MDEV-28634... and all of that without needing to actually do any TLS cracking.For all I know, the NSA or CSIC or GCHQ or יחידה 8200 or the Chinese/Iranian/Indian/Russian/$COUNTRY equivalents have already figured this out themselves, and have been MITM'ing MariaDB connections on the Internet at massive scale for years.
Attachments
Issue Links
- includes
-
CONC-656 TLS-using MariaDB clients tell MITM attackers if they can be undetectably MITM'ed
-
- Closed
-
- relates to
-
MDEV-31585 Server improperly requires client capability bits to be sent IN PLAINTEXT prior to TLS handshake
-
- Open
-
-
CONC-648 Client improperly accepts error packets prior to TLS handshake
-
- Closed
-
- links to
Activity
| Link | This issue relates to MDEV-31585 [ MDEV-31585 ] |
| Attachment | screenshot-1.png [ 70781 ] |
| Attachment | screenshot-2.png [ 70782 ] |
| Summary | Client improperly sends identifying information in plaintext prior TLS handshake | Client improperly sends identifying information in plaintext prior to TLS handshake |
| Description |
... and, furthermore, the server {color:red}trusts that information{color} and irreversibly updates its assessment of the client capabilities for this connection: (*todo MDEV-????*)
Spinning this off from my [comment|https://jira.mariadb.org/browse/CONC-648?focusedCommentId=263365#comment-263365] on As I showed there, MariaDB clients including Connector/C, send a great deal of identifying information about themselves {color:red}in plaintext{color} in the initial "login request" packet, even if they subsequently switch to TLS: !https://jira.mariadb.org/secure/attachment/70760/screenshot-1.png! This information includes the client capability bits, the client's {{MAX_ALLOWED_PACKET}} size, and the client's *charset*. Copying from there: {quote}This makes MariaDB client-server connections an _extraordinarily_ exploitable and target-rich environment for pervasive MITM attackers. A government agency could, for example, fingerprint the plaintext client+server greeting packets to determine the exact versions, pull out the ones that appear to be from interesting parts of the world based on the plaintext [preferred client charset|https://mariadb.com/kb/en/supported-character-sets-and-collations], and manipulate them in various ways with MITM and downgrade attacks using this vulnerability, as well as the long-known For all I know, the NSA or CSIC or GCHQ or יחידה 8200 or the Chinese/Iranian/Indian/Russian/$COUNTRY equivalents have already figured this out themselves, and have been MITM'ing MariaDB connections on the Internet at massive scale for years.{quote} |
... and, furthermore, the server {color:red}requires that information to be sent in plaintext{color}, and irreversibly updates its assessment of the client capabilities for this connection based on it: todo MDEV-31585
Spinning this off from my [comment|https://jira.mariadb.org/browse/CONC-648?focusedCommentId=263365#comment-263365] on As I showed there, MariaDB clients including Connector/C, send a great deal of identifying information about themselves {color:red}in plaintext{color} in the initial "login request" packet, even if they subsequently switch to TLS: !https://jira.mariadb.org/secure/attachment/70760/screenshot-1.png! This information includes the client capability bits, the client's {{MAX_ALLOWED_PACKET}} size, and the client's *charset*. Copying from there: {quote}This makes MariaDB client-server connections an _extraordinarily_ exploitable and target-rich environment for pervasive MITM attackers. A government agency could, for example, fingerprint the plaintext client+server greeting packets to determine the exact versions, pull out the ones that appear to be from interesting parts of the world based on the plaintext [preferred client charset|https://mariadb.com/kb/en/supported-character-sets-and-collations], and manipulate them in various ways with MITM and downgrade attacks using this vulnerability, as well as the long-known For all I know, the NSA or CSIC or GCHQ or יחידה 8200 or the Chinese/Iranian/Indian/Russian/$COUNTRY equivalents have already figured this out themselves, and have been MITM'ing MariaDB connections on the Internet at massive scale for years.{quote} |
| Description |
... and, furthermore, the server {color:red}requires that information to be sent in plaintext{color}, and irreversibly updates its assessment of the client capabilities for this connection based on it: todo MDEV-31585
Spinning this off from my [comment|https://jira.mariadb.org/browse/CONC-648?focusedCommentId=263365#comment-263365] on As I showed there, MariaDB clients including Connector/C, send a great deal of identifying information about themselves {color:red}in plaintext{color} in the initial "login request" packet, even if they subsequently switch to TLS: !https://jira.mariadb.org/secure/attachment/70760/screenshot-1.png! This information includes the client capability bits, the client's {{MAX_ALLOWED_PACKET}} size, and the client's *charset*. Copying from there: {quote}This makes MariaDB client-server connections an _extraordinarily_ exploitable and target-rich environment for pervasive MITM attackers. A government agency could, for example, fingerprint the plaintext client+server greeting packets to determine the exact versions, pull out the ones that appear to be from interesting parts of the world based on the plaintext [preferred client charset|https://mariadb.com/kb/en/supported-character-sets-and-collations], and manipulate them in various ways with MITM and downgrade attacks using this vulnerability, as well as the long-known For all I know, the NSA or CSIC or GCHQ or יחידה 8200 or the Chinese/Iranian/Indian/Russian/$COUNTRY equivalents have already figured this out themselves, and have been MITM'ing MariaDB connections on the Internet at massive scale for years.{quote} |
... and, furthermore, the server {color:red}requires that information to be sent in plaintext{color}, and irreversibly updates its assessment of the client capabilities for this connection based on it (see MDEV-31585).
Spinning this off from my [comment|https://jira.mariadb.org/browse/CONC-648?focusedCommentId=263365#comment-263365] on As I showed there, MariaDB clients including Connector/C send a great deal of identifying information about themselves {color:red}in plaintext{color} in the initial "login request" packet, even when they subsequently switch to TLS, and then resend a login request packet over the TLS channel: !https://jira.mariadb.org/secure/attachment/70760/screenshot-1.png! This information includes the client capability bits, the client's {{MAX_ALLOWED_PACKET}} size, and the client's *charset*. Copying from there: {quote}This makes MariaDB client-server connections an _extraordinarily_ exploitable and target-rich environment for pervasive MITM attackers. A government agency could, for example, fingerprint the plaintext client+server greeting packets to determine the exact versions, pull out the ones that appear to be from interesting parts of the world based on the plaintext [preferred client charset|https://mariadb.com/kb/en/supported-character-sets-and-collations], and manipulate them in various ways with MITM and downgrade attacks using this vulnerability, as well as the long-known For all I know, the NSA or CSIC or GCHQ or יחידה 8200 or the Chinese/Iranian/Indian/Russian/$COUNTRY equivalents have already figured this out themselves, and have been MITM'ing MariaDB connections on the Internet at massive scale for years.{quote} |
| Description |
... and, furthermore, the server {color:red}requires that information to be sent in plaintext{color}, and irreversibly updates its assessment of the client capabilities for this connection based on it (see MDEV-31585).
Spinning this off from my [comment|https://jira.mariadb.org/browse/CONC-648?focusedCommentId=263365#comment-263365] on As I showed there, MariaDB clients including Connector/C send a great deal of identifying information about themselves {color:red}in plaintext{color} in the initial "login request" packet, even when they subsequently switch to TLS, and then resend a login request packet over the TLS channel: !https://jira.mariadb.org/secure/attachment/70760/screenshot-1.png! This information includes the client capability bits, the client's {{MAX_ALLOWED_PACKET}} size, and the client's *charset*. Copying from there: {quote}This makes MariaDB client-server connections an _extraordinarily_ exploitable and target-rich environment for pervasive MITM attackers. A government agency could, for example, fingerprint the plaintext client+server greeting packets to determine the exact versions, pull out the ones that appear to be from interesting parts of the world based on the plaintext [preferred client charset|https://mariadb.com/kb/en/supported-character-sets-and-collations], and manipulate them in various ways with MITM and downgrade attacks using this vulnerability, as well as the long-known For all I know, the NSA or CSIC or GCHQ or יחידה 8200 or the Chinese/Iranian/Indian/Russian/$COUNTRY equivalents have already figured this out themselves, and have been MITM'ing MariaDB connections on the Internet at massive scale for years.{quote} |
... and, furthermore, the server {color:red}requires that information to be sent in plaintext{color}, and irreversibly updates its assessment of the client capabilities for this connection based on it (see MDEV-31585).
Spinning this off from my [comment|https://jira.mariadb.org/browse/CONC-648?focusedCommentId=263365#comment-263365] on As I showed there, MariaDB clients including Connector/C send a great deal of identifying information about themselves {color:red}in plaintext{color} in the initial "login request" packet, even when they subsequently switch to TLS, and then resend a login request packet over the TLS channel: !https://jira.mariadb.org/secure/attachment/70760/screenshot-1.png! This information includes the client capability bits, the client's {{MAX_ALLOWED_PACKET}} size, and the client's *charset*. Copying from there: {quote}This makes MariaDB client-server connections an exploitable and target-rich environment for pervasive MITM attackers. A government agency could, for example, fingerprint the plaintext client+server greeting packets to determine the exact versions, pull out the ones that appear to be from interesting parts of the world based on the plaintext [preferred client charset|https://mariadb.com/kb/en/supported-character-sets-and-collations], and manipulate them in various ways with MITM and downgrade attacks using this vulnerability, as well as the long-known For all I know, the NSA or CSIC or GCHQ or יחידה 8200 or the Chinese/Iranian/Indian/Russian/$COUNTRY equivalents have already figured this out themselves, and have been MITM'ing MariaDB connections on the Internet at massive scale for years.{quote} |
| Remote Link | This issue links to "mariadb-connector-c PR#227 (Web Link)" [ 35487 ] |
| Remote Link | This issue links to "MariaDB server PR#2684 (Web Link)" [ 35488 ] |
| Attachment | screenshot-3.png [ 70844 ] |