Ah ok I understand why it was closed then. Interesting that your not seeing this issue.
I have attached screenshots of a couple systems with this issue:
Server version: 10.6.5-MariaDB-1:10.6.5+maria~focal
Server version: 10.3.31-MariaDB-0+deb10u1 Raspbian 10
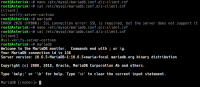
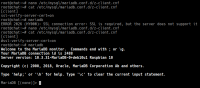
I have to keep
ssl-verify-server-cert=on
|
so that my connection to REMOTE sql servers use SSL.
connecting using a unix socket to my LOCAL instance of mariadb server(does not have a cert of any kind) does not work, it should not enforce the requrement of the server needing a cert when I am trying to use a unix socket.
I think what your are saying is that your LOCAL mariadb has a cert, and so ssl-verify-server-cert=on works perfectly fine.
what I am saying that my LOCAL mariadb has no cert at all! only my remote mariadb server has a cert (thats the only place I am needing one, as thats the only server accepting remote connections)
so my Local Mariadb server does not have a cert
my Remote Mariadb server does have a cert from let's encrypt.
I have defined ssl-verify-server-cert=on so that my client can connect to the Remote Mariadb server which does have the let's encrypt cert.
because I have defined ssl-verify-server-cert=on my client cannot connect using a unix socket to the Local Mariadb server which does not have a cert of any kind (and does not need a cert because it is not accepting remote connections)
I hope the extra information paints a clearer picture of exactly what the problem is that I am having. This problem does not exist using mysql-client only if using mariadb-client.
mariadb the way you enforce the client to use SSL is by using ssl-verify-server-cert=on
mysql you use tls_version=TLSv1.2,TLSv1.3 instead for the client config.
under mysql you can connect using unix socket to your local sql server even with tls_version=TLSv1.2,TLSv1.3 in place, even if your local sql server does not have a cert! This is the way mariadb-client also used to work, but not anymore.
The goal of all of this is to be able to enforce my client to connect to remote sql servers using SSL, but when im connecting to my local instance using a unix socket, allow me to connect to it.
otherwise on all machines where I use ssl-verify-server-cert=on I would also have to put a cert, regardless if they are accepting remote connections, this seems like a major design flaw as it currently sits.
Bug
Major


I have a remote Mariadb server that uses a Let's Encrypt Cert
so on my client I want to make sure I access that remote server using SSL:
nano /etc/mysql/mariadb.conf.d/z-client.cnf[client]ssl-verify-server-cert=onso now when I do
mysql -u remoteuser -p -h remotehost.example.comit works and connects using SSL! YAY!
BUT WAIT! what if I want to use my client to connect to the local instance of mariadb server instead of the remote instance.....
mormally I would just do it this way and it would connect using the unix socket.
sudo mysqlhowever because of the client configuration this no longer works:
nano /etc/mysql/mariadb.conf.d/z-client.cnf[client]ssl-verify-server-cert=onThis is not an issue with Mysql-client only mariadb-client.
in mysql client you configure it to use SSL by doing this:
nano /etc/mysql/mysql.conf.d/mysqld.cnf[client]tls_version=TLSv1.2,TLSv1.3with that in place you can connect to remote hosts using SSL!
BUT you can also still access your local instance of sql server using sudo mysql to use the unix socket!
I am surprised this was closed as its still an issue for me and I am on 10.6.x
Please don't suggest using self signed certs just to use the unix socket.... thats a workaround and not what im looking for, theres no reason to use certs on a unix socket when I am connecting from and to the same machine using sudo mysql