We're running Ubuntu 18.04 LTS with MariaDB 10.3.16 configured with SSL/TLS support and `REQUIRE SSL` on all accounts. We have a lots of Mac clients accessing our MariaDB servers and most of them are using nightly builds Sequel Pro, arguably the most popular MySQL client in the macOS world. (Nightly builds because the Sequel Pro project is struggling with release management and maintenance).
Today I attempted to upgrade one of our MariaDB servers to MariaDB 10.4.6 only to find out that Sequel Pro no longer was able to connect with SSL/TLS (only establishing an SSL/TLS session and verifying the remote peer certificate; the server is not using client cert authentication).
Unfortunately I no longer have the exact error message at hand that Sequel Pro reported but it said something about the connection failed and that the SSL error number was unknown (or zero).
Typically this means that the SSL/TLS handshake failed, and most often this is related to cipher suite selection and/or key-exchanges.
Here's the relevant SSL/TLS configuration on our MariaDB server:
[mysqld]
ssl = On
ssl-ca = /etc/mysql/xxx-mysql-ca.pem
ssl-cert = /etc/mysql/replica-XYZ.example.com.crt
ssl-key = /etc/mysql/replica-XYZ.example.com.key
We use TLS extensively in our network to ensure privacy (encryption in transit), authentication and integrity, so the SSL/TLS issues in MySQL clients are a blocker for us.
I noticed there was a mention of the SSL/TLS library in the most recent release notes:
I also note that you link to a page on your SSL/TLS support (kudos!) here:
It seems that you've switched to wolfSSL from yaSSL (good riddance!) in MariaDB 10.4.6. While I haven't tried earlier versions of the 10.4 series, perhaps the change to wolfSSL might be related to the issues with Sequel Pro. (That doesn't mean I'd like you to switch back to yaSSL because most likely the problem is related to the selection of cipher suites and/or keyexchange.)
FWIW, over the years we've run into many SSL/TLS related issues with both MySQL servers and MySQL clients. MySQL's use of yaSSL has been a problem (it's under developed and doesn't support modern TLS very well). On the Windows side, SChannel has a bug with respect to DH (Diffie-Hellman) key-exchanges and some cipher suites (I think this is mentioned in Georg's comment in MDEV-13492). Default installations of HeidiSQL often experience SSL/TLS handshake failures with until you replace the shipped libmysql.dll with a specific version and drop the bundled libmariadb.dll file (see e.g. https://www.heidisql.com/forum.php?t=19494 and https://github.com/HeidiSQL/HeidiSQL/issues/519).
It would be great if the SSL/TLS issues with popular MySQL clients (Sequel Pro on macOS and HeidiSQL on Windows) could be worked out so that it's possible to connect to MariaDB 10.4. (Note that I didn't test HeidiSQL with MariaDB 10.4.)
Perhaps any workarounds found for this issue can be posted here?
Bug
Major
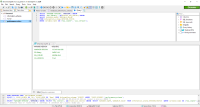
I fired up Wireshark and noticed that Sequel Pro is attempting to negotiate TLSv1.0, which is disabled by default starting with MariaDB 10.4.6.
1. The change to supported TLS versions should really be documented on https://mariadb.com/kb/en/library/upgrading-from-mariadb-103-to-mariadb-104/
2. The docs on https://mariadb.com/kb/en/library/ssltls-system-variables/#tls_version suggests that the default value is "TLSv1.1,TLSv1.2,TLSv1.3". Furthermore it says that valid values are "TLSv1.0, TLSv1.1, TLSv1.2, TLSv1.3". If copy-pasting the valid values part, you get a spaced list which will cause MySQL to fail startup with an unhelpful message such as "[ERROR] /usr/sbin/mysqld: Error while setting value 'TLSv1.0, TLSv1.1, TLSv1.2, TLSv1.3' to 'tls_version'". The documentation should be more clear that the list mustn't contain whitespace.
3. A default install of HeidiSQL 10.2 on Windows 10 attempts to negotiate TLS v1.2, with the server selecting TLS_DHE_RSA_WITH_AES_256_CBC_SHA (0x0039). Unfortunately the connection fails after the Client Key Change+Change Chiper Spec messages. It seems the server aborts the connection with a fatal TLS error of "unknown message". The only thing logged by MariaDB is "[Warning] Aborted connection 47 to db: 'unconnected' user: 'unauthenticated' host: '192.168.2.2' (This connection closed normally without authentication)".
4. By removing libmariadb.dll from C:\Program files\HeidiSQL the client will fall back to using the bundled libmysql 5.6.6.0. Now the client attempts to negotiate TLS 1.0 with the server selecting the cipher TLS_DHE_RSA_WITH_AES_256_CBC_SHA (0x0039). Unfortunately the connection fails in a similar manner as when relying on libmariadb.dll. With MariaDB 10.3 installations I've had success connecting from HeidiSQL with libmariadb.dll removed and using a libmysql.dll version 5.7.17.